A Guide to OAuth 2.0 and OpenID Connect.
Comprehend the most commonly used authorization and authentication protocols work.
Ever wondered what happens when you click on "Sign up with Google" or "Sign up with Facebook" on any third-party apps that request data from Google/Facebook? This guide is for you to understand the basics of the most widely used auth protocols.
OAuth 2.0 vs OpenID Connect
OAuth 2.0 is used for authorization purposes whereas OpenID Connect is used for authentication. OpenID Connect is an identity layer on top of the OAuth 2.0 protocol. It extends OAuth 2.0 to standardize a way for authentication.
OAuth 2.0
OAuth 2.0 is an Open Authorization protocol to allow secure authorization in a simple and standard method from web, mobile, and desktop applications. It allows applications to access user data without the user’s password. Before OAuth, the only way to delegate access to user data is via sharing passwords. Obviously, none of us will share passwords to some shady applications and compromise security.
Now we know the importance of OAuth, let's deep dive into the protocol.
OAuth 2.0 Terminology
To understand the protocol, we need to know the basic terminology used.
- Resource Owner : It's you who owns the data and shares it with other third-party applications.(eg: The owner of Google/Facebook/Microsoft accounts)
- Client : The third-party application that wants access to your data.
- Authorization Server : The application that already knows the resource owner.
- Resource Server : The service the client wants to use on behalf of the resource owner. Sometimes the authorization server and resource server are the same servers.
- Redirect URI : The URL, the authorization server will redirect the resource owner back to the client after granting permissions.
- Response Type : The type of information the client expects to receive. The most common response type is
code. - Scope : The granular permission the client defines to access the resource server.
- Client ID : The unique ID defined by the authorization server to identify the client.
- Client Secret : The secret password that only the client and the authorization server know. This allows them to share the information securely.
- Authorization Code : A short-lived temporary code the authorization server sends back to the client. The client then sends back the code along with the client secret in exchange for an access token.
- Access Token : This is the key, the client will use to communicate with the resource server.
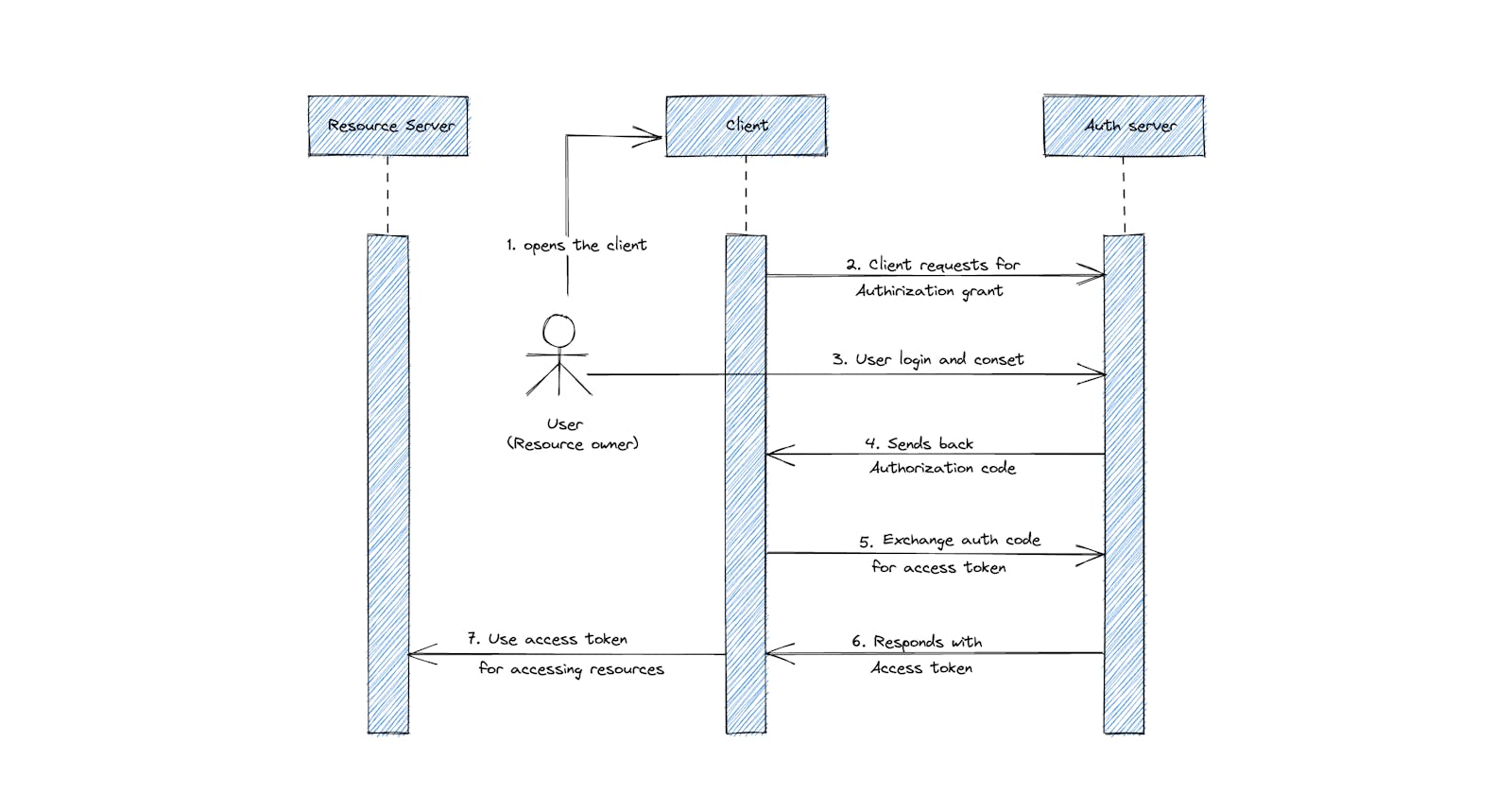
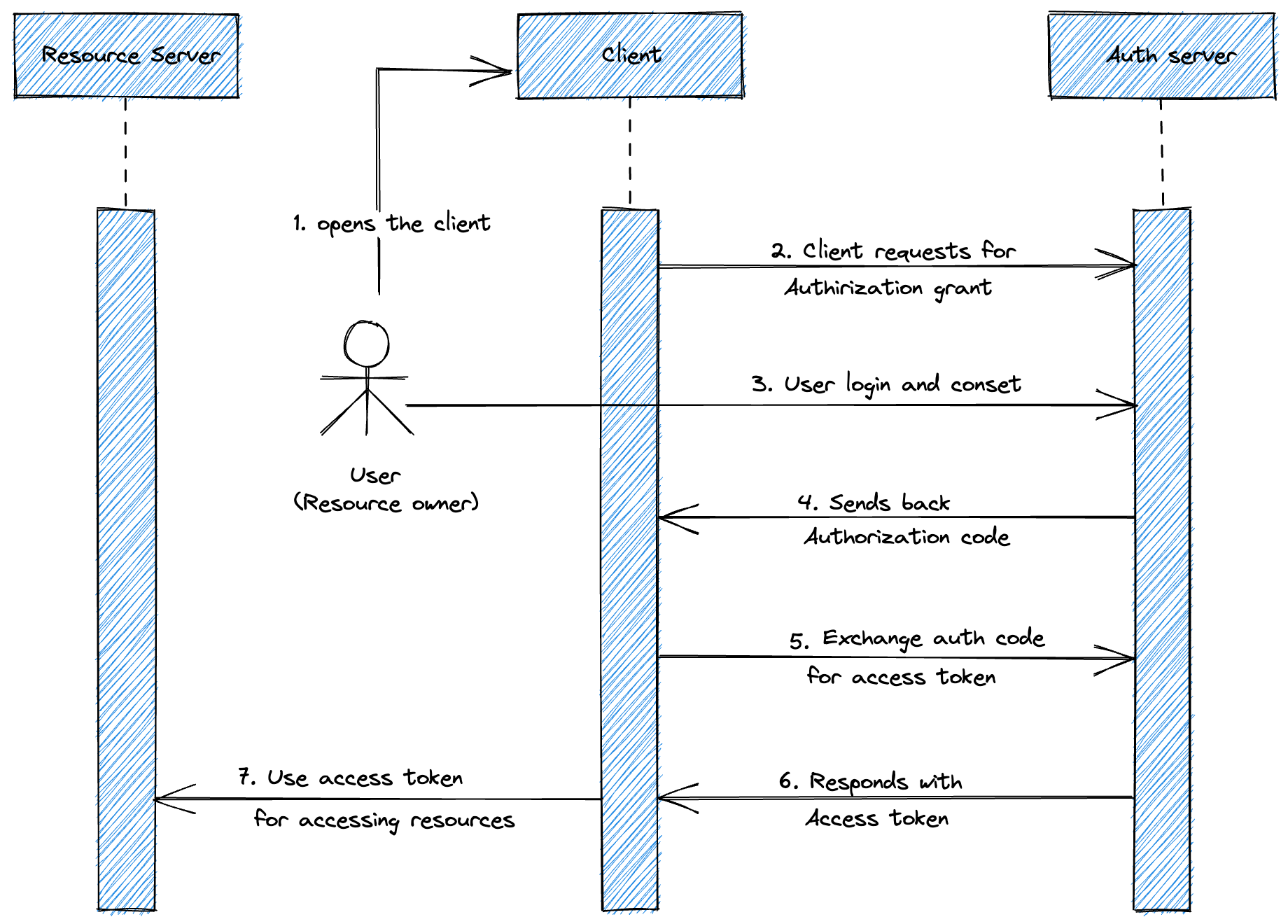
OAuth 2.0 authorization flow
Basically, the two most commonly used OAuth 2.0 flows are authorization code flow for server-based applications and implicit flow for pure JavaScript Single Page Applications (SPAs). Below is the authorization code flow for server-based applications.
The implicit flow for SPAs doesn't require additional authorization code call to the authorization server, because most static sites don't have an explicit backend. In the implicit flow, the authorization server responds with an access token right away.
OpenID Connect
OpenID Connect is a simple identity layer on top of the OAuth 2.0 protocol. It allows clients to verify the identity of the end-user based on the authentication performed by an authorization server.
While OAuth 2.0 is about resource access and sharing, OIDC is about user authentication. Its purpose is to give you one login for multiple sites. Each time you need to log in to a website using OIDC, you are redirected to your OpenID site where you log in, and then taken back to the website.